 |
|||
 |
|||
| CS 354 | Computer Organization and Systems | Fall 2019 |  |
 |
|||
 |
|||
Project 6 - Monte Carlo Computation of Pi using MIPS Floating PointGoalsIn this project you will work with programming MIPS to use floating point data and instructions to compute pi. Floating Point in MIPSAs we have seen, there are different representations for integer and real numbers. We have seen several ways of manipulating integers and this project will focus on floating point values. Like most computer systems today, MIPS uses the IEEE-754 standard to represent both single precision (32 bit) and double precision (64 bit) floating-point representations. The MIPS intructions are described in Appendix B (starting on page B-73). Floating-point operations are performed on a floating-point coprocessor that contains 32 general purpose floating point registers, $f0 through $f31 (click the Coproc 1 tab in MARS to see these registers). Each register holds only 32 bits, only enough for a single precision value. Double precision values are stored in two adjacent registers, and are referred using the smallest register number. For example, a double precision value stored in $f0 and $f1 would be referred to as $f0. Imagine you would like to convert a temperature in degrees Celsius to degrees Fahrenheit. The program float.s shown below illustrates one way to do this. Download and run this program, stepping through the program and watch the memory and the register values change.
Here are some important things to note about the above program. There are floating point instructions for single precision and double precision, specified using either .s or .d respectively. Note the .float directive in the .data section can be used to store floating point values in memory that can be loaded into a floating point register using the l.s instruction. There are no immediate type floating point instructions (can you imagine why not?). A wide variety of comparisons are available (similar to beq, bne, etc) that set a flag in the floating point coprocessor. One of these is the c.lt.s instruction, which sets the flag if the first operand is less than the second operand. The flag can be checked using the bclf instruction, which branches if the flag is false; bclt branches if the flag true. Also, note there are specific system calls for reading and printing floating point values. Pseudo-Random NumbersMost computer languages provide a mechanism for producing random numbers called a random number generator (RNG). These random number generators produce numbers that are deterministically computed therefore are not truly random. In fact there are no truly random numbers available on a computer, because computers always produce the same results for a given set of inputs. A complete discussion of how computers compute pseudo-random numbers is beyond this project, but see the Knuth reference or talk to me if you are interested in learning more. Pseudo-Random Numbers in MARS-MIPSThe MARS simulator has available a few system calls related to random numbers (these are not available in SPIM). Of particular importance in our application here is setting the initial seed value, setting the range of random numbers, and obtaining random numbers. The program random.s shown below illustrates how to compute random numbers in MIPS using MARS.
Monte Carlo algorithmsMonte Carlo algorithms, unlike deterministic algorithms, use statistical sampling to perform a computation. The name was coined in the 1940's for the famous European casino in Monaco, one of the world's great monuments to probability. Like other algorithmic paradigms, Monte Carlo algorithms have a particular areas where they are effective. Normally Monte Carlo methods are used when no deterministic algorithm exists or the deterministic algorithm is intractable. Monte Carlo algorithms have the following structure
PiThe mathematical constant Pi (3.14159265...) is probably the most famous mathematical constant and is found in many areas of mathematics. For example, given any circle, Pi is the ratio of the circumference of the circle to its diameter. Pi is transcendental, meaning it is not the root of any polynomial with algebraic (non-transcendental) coeffiecients. See Pi Formulas at the MathWorld website for some other formulas for Pi. Because Pi is transcendental, the decimal expansion can never be fully expanded and any value given can only be approximate. Archimedes was able to approximate Pi to 3.1419 (200 BC). Later, Pi was approximated using perimeters of regular polygons inscribed inside and circumscribed outside a given circle. Once calculus was developed, infinite series techniques were used to refine the approximations. Von Neumann used ENIAC in 1949 to compute over 2000 digits of Pi. In 2005, a group at the University of Tokyo (www.super-computing.org) computed over 1 trillion digits of Pi. Surprising Pi fact: the BBP Formula can be used to exactly compute the nth digit of Pi base 16. Monte Carlo Simulation of PiInterestingly, one of the first Monte Carlo methods was described by Buffon in 1777. Simply stated, what is the probability that a needle of length L will intersect the intersection between planks of width D when placed at random on an infinite wood plank floor. Surprisingly, if L=D the probability of intersection turns out to be 2/Pi. Assuming L=D, one simply drops N needles on the floor and counts the number of intersections T, then Pi can then be approximated by 2T/N. A simpler Monte Carlo method to compute the value of Pi uses some very basic geometric relationships. Consider a circle of radius R inscribed in a square with a side length of 2R. 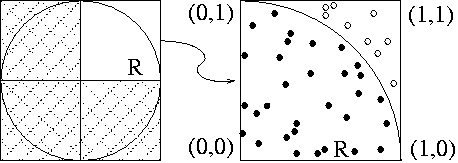
Consider a random point (x,y) in the quadrant. Note the probability it is below the curve is simply the area of the region under the curve compared to the total area of the quadrant. This is simply Pi/4. To compute Pi using this method, one needs to generate N random points (x,y) in the quadrant. Count the number of these points that are below the curve (x2 + y2 < R2), a "hit", call this number S. Pi/4 can be approximated as the number of hits divided by the total number of points generated by noting that S/N approaches Pi/4 as N goes to infinity. So 4S/N will be an approxiamte value for Pi. In the above figure N=40 and S=31, so Pi would be computed as 4·31/40 = 3.1. TaskWrite a MIPS program that computes Pi using the Monte Carlo method described above. Generate a random x value, a random y value, then determine if the corresponding point falls under the curve. If so, increment the number of hits. Use the largest N you can, say 1000000 (you might want to start with something like 40). DeliverablesSend me an email with the MIPS file containing your program. Comment each line and code segment explaining its function. References
Copyright © 2019, David A. Reimann. All rights reserved. |